One Of The Best Info About How To Detect Confiker

However, there is a free, easy way to detect and remove it:
How to detect confiker. Felix and i had a discussion with dan kaminsky about the. Brief overview of the conficker worm and how the languardian can be used to detect its presence Checks if a host is infected with conficker.c or higher, based on conficker's peer to peer communication.
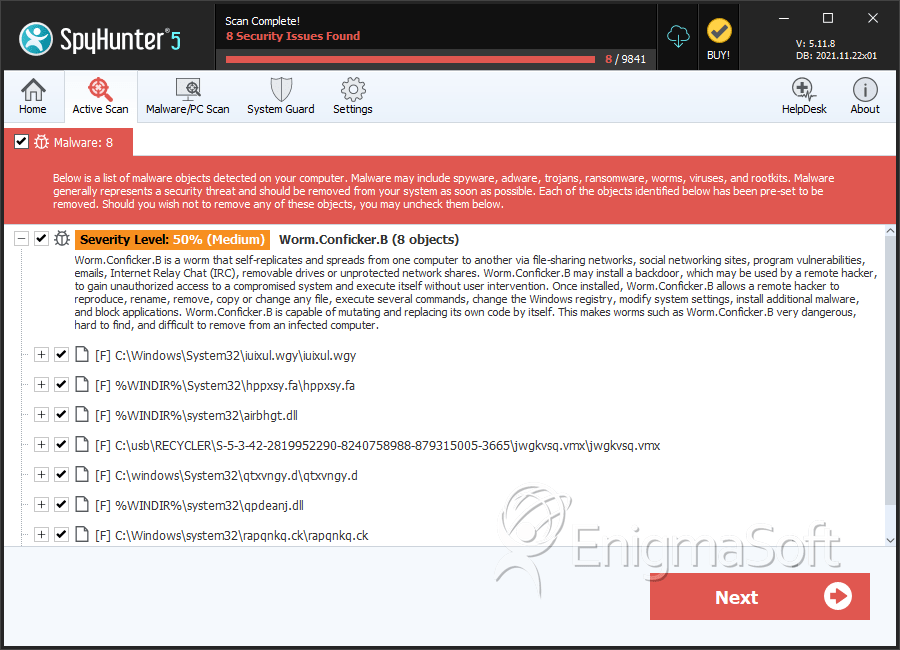
To remove infected files, run the tool. 1 comment 1 solution 929 views last modified: Here is what you need to look for in regards to conficker.
How to detect conficker a. It requires that “probe services on every port” be enabled. In the nessus scan policy.
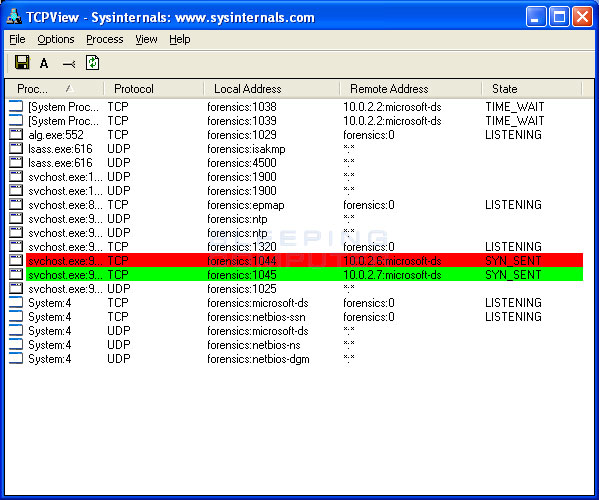
Start the logging within wireshark. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. Up to 10% cash back download conficker worm fix.
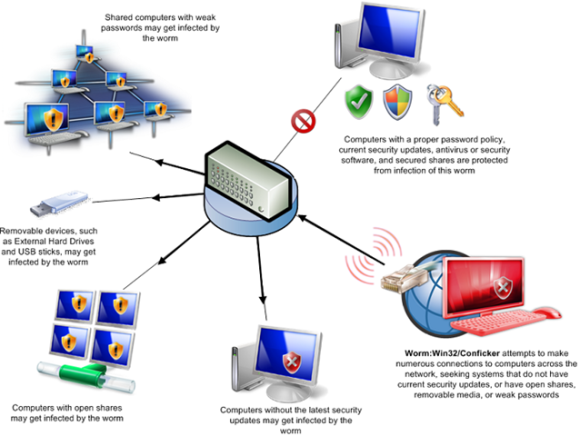
Download our free removal tool: If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands: Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008.
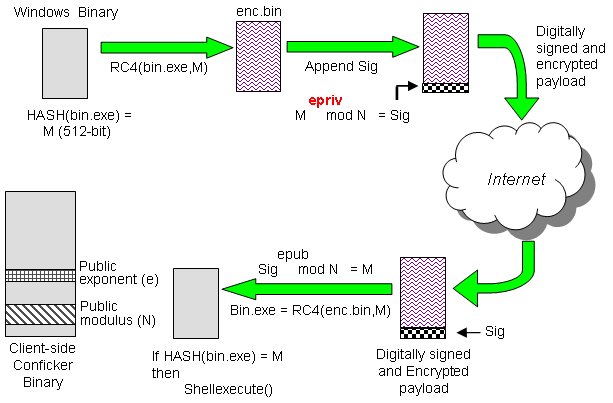
When conficker.c or higher infects a system, it opens four ports: Malware like zeus, conficker and many others use dgas (domain generation algorithms) to build resilient c2 servers. In practice, once a computer gets infected, the hacker.











/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)